Targets
A target is the URL of a Web Application, Website, or API.
Scan your Web Applications to discover external vulnerabilities.
The complexity of today’s applications, combined with the constant evolution of cyber threats, makes it increasingly difficult to ensure security measures. Traditional methods of security assessment often fall short of providing continuous insights, leading to potential blind spots.
The DAST Scanner addresses these challenges head-on. By combining the power of PtaaS with DAST, you gain a comprehensive solution for continuously assessing risk.
To get started with the DAST Scanner, you will need to add a target. Every Cobalt Customer has access to one target for free unlimited scanning. Additional targets can be purchased. Learn more about targets.
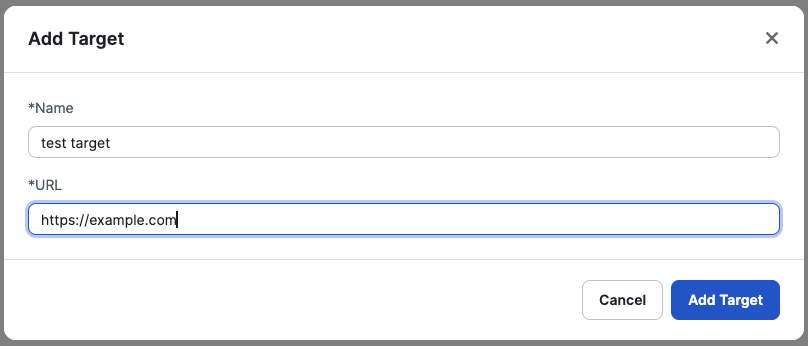
See more about how to configure a target in configuring a target
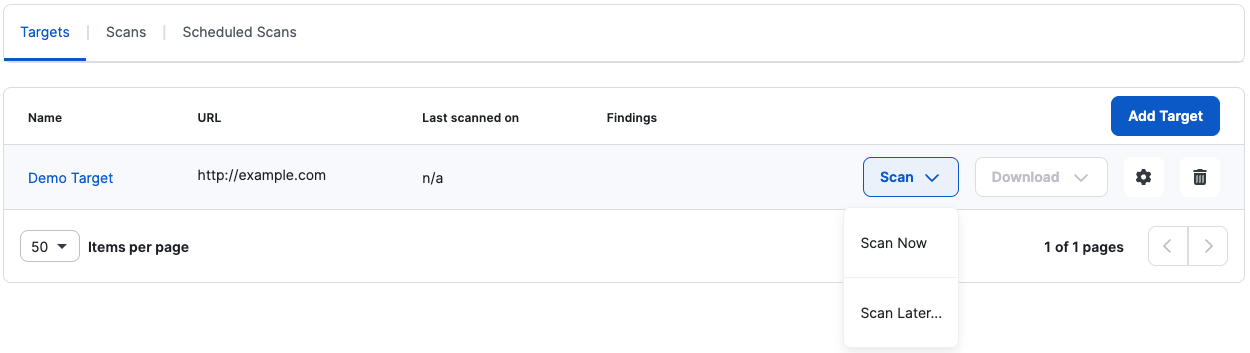
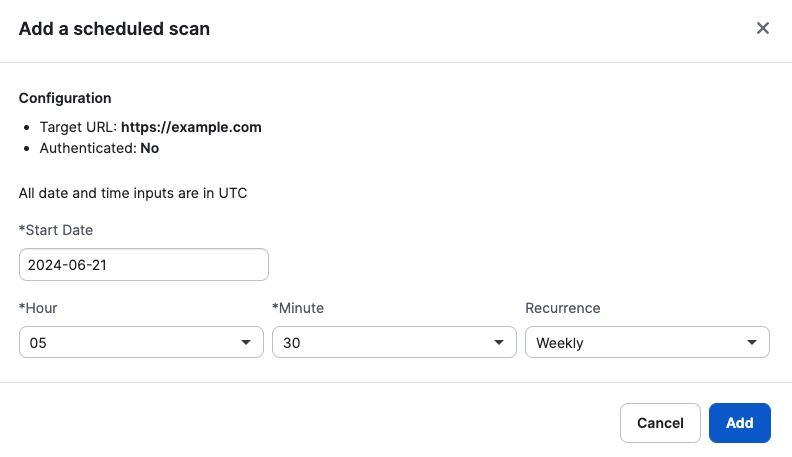
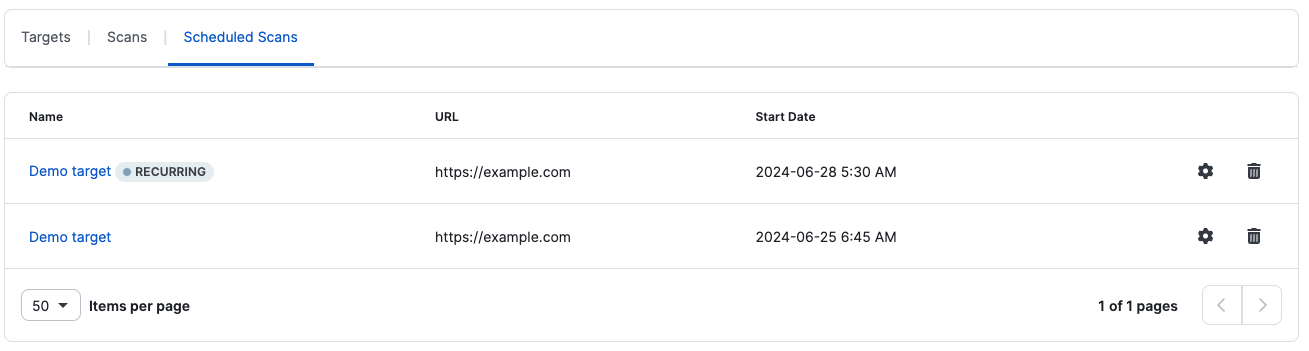
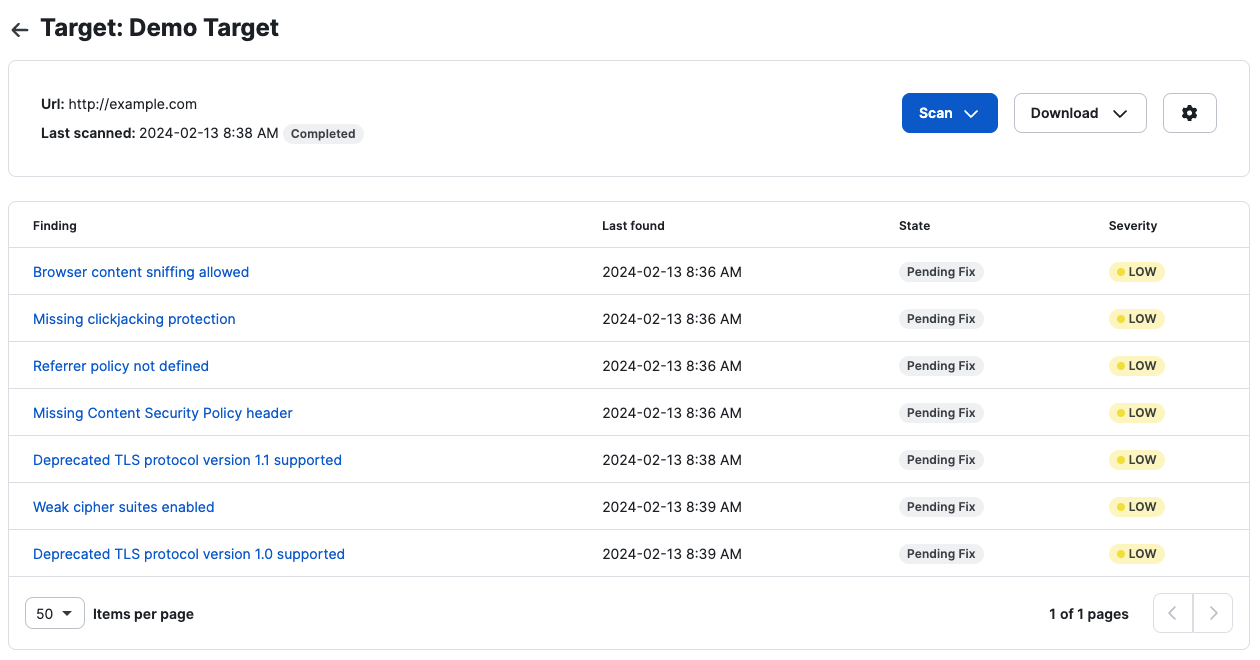
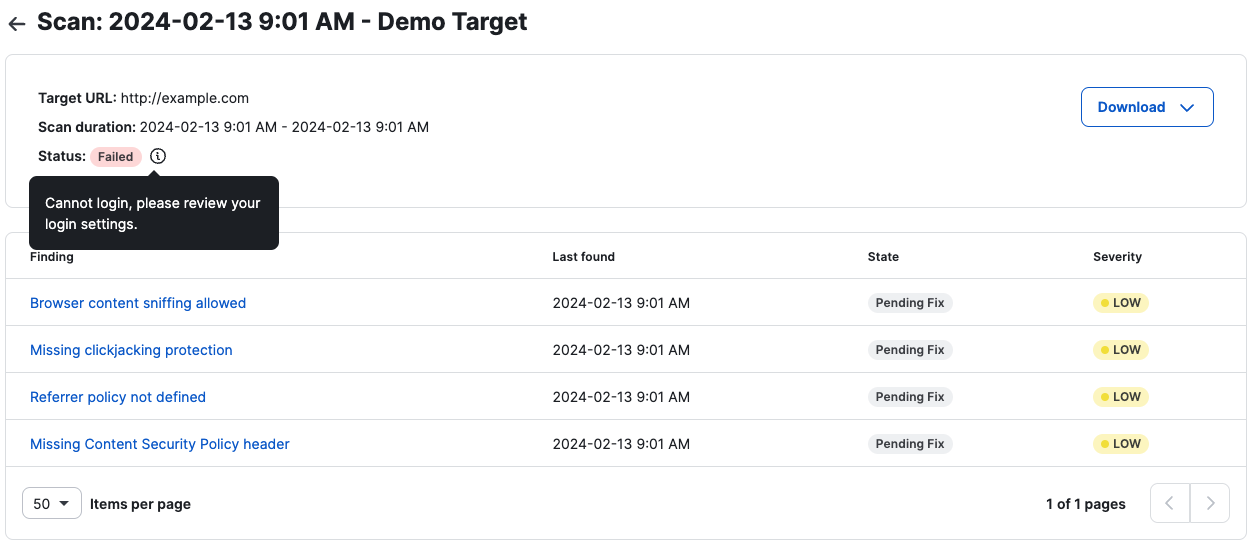
Once a scan is complete, you have two options to View Results
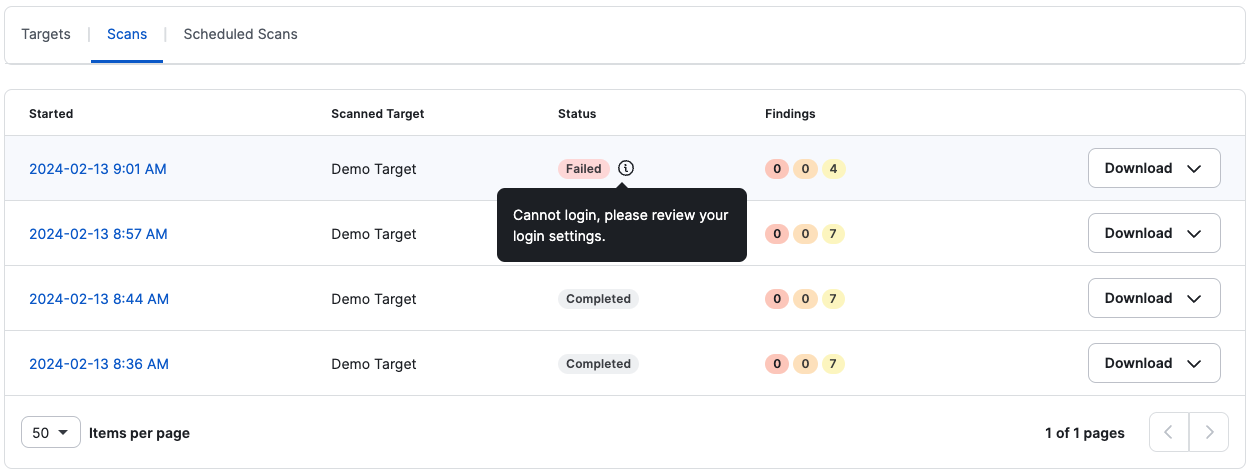
If the scan fails, navigate to the scans list or the scan details page to see the reason for the failed scan(s).
Scan List View:
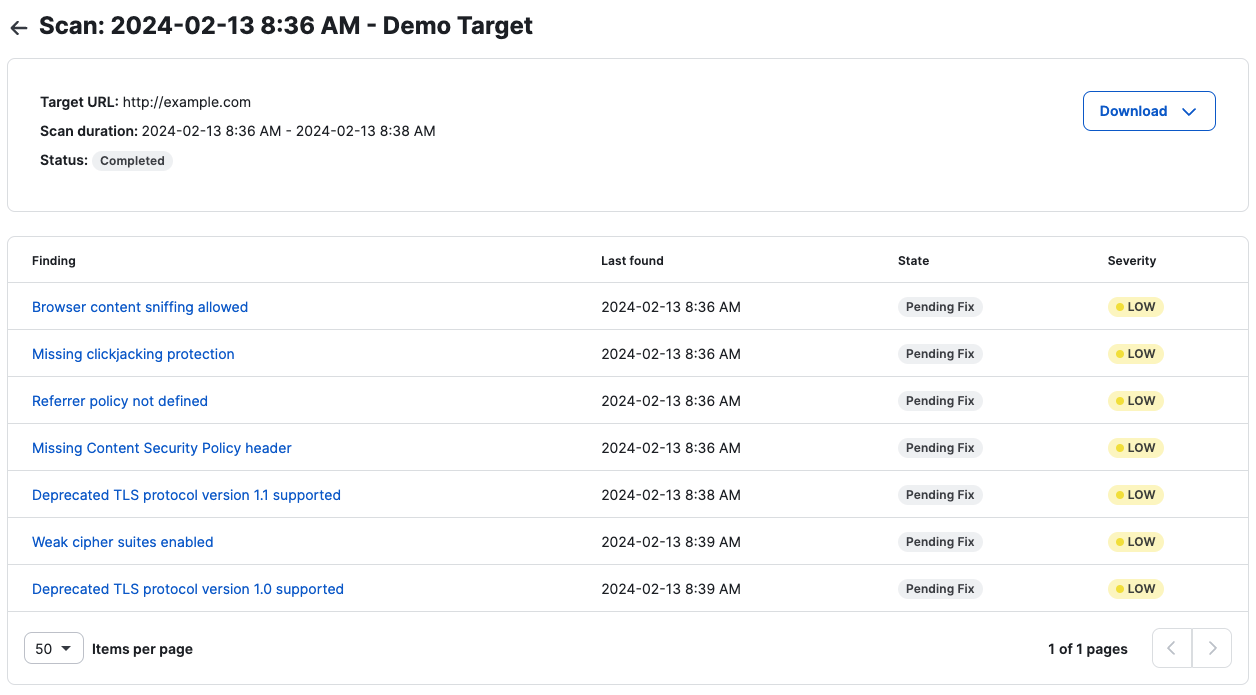
Scan Details View:
Move Finding State
Retest Finding

For compliance and to better understand the results of your scans, we provide different types of scans.
From Targets, click Download to select the report you want to download:
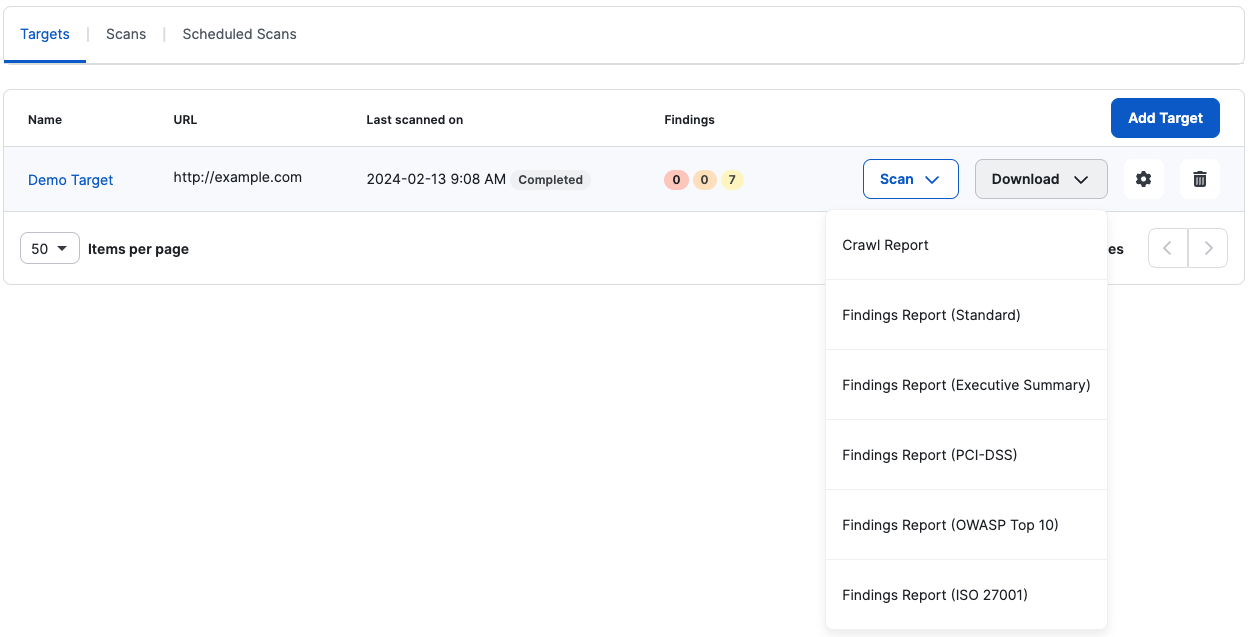
You can also do this from the scans list or the scan details page.
There are different report types that you can download from a scan. Note that for failed scans, reports are not available. Most of these reports are PDF reports, except for the crawl report, which is a CSV file.
It is the default report type and contains:
It is a high-level view report of the scan and only contains:
It is a scan report specific to PCI-DSS compliance. You can use this report to verify which controls a target is passing or failing. PCI-DSS is like the Standard report but adds a section to the scan summary with the PCI-DSS requirements checklist.
The report indicates if a target was tested for the requirements checklist and if it passed each item on the list.
It is similar to the PCI-DSS report but considers the most recent OWASP Top 10. OWASP Top 10 scan report uses a popular framework provided by OWASP that lists the top 10 security risks of web applications. Auditors often use this framework when performing a company’s security audit.
It is a specific scan report on compliance with ISO/IEC 27001 (2022 revision). You can use this report to verify which controls a target is passing or failing. ISO 27001 is like the standard report but adds a section to the scan summary with the ISO 27001 requirements checklist.
The report indicates if a target was tested for the requirements checklist and if it passed each item on the list.
The crawl or coverage report lists URLs that were scanned along with ones that weren’t scanned. This acts as a tool for you to check if the scanner is reaching every endpoint possible and filtering them successfully. This report is a CSV file, which you can export to Excel or any similar tool that you use.
Before and while doing tests, the crawler will navigate your website to find every endpoint possible while testing every input it might find. Then those URLs are sent to the scanner to be tested for any vulnerabilities.
Coverage is a fundamental aspect of a scan, as it may be the difference between a useful, successful scan and an uninformative scan.
For support, please reach out to your CSM or email us at dast@cobalt.io.
A target is the URL of a Web Application, Website, or API.
More information about target authentication fields and hacks
More information about login sequence recorder
Add extra hosts to include further domains in Web Application scans.
Push DAST findings to your ticketing system!