Set Up an In-House Pentest
This page is for users who manage in-house pentests for their organization. If you’re an In-House Pentester, please read how to complete a pentest.
An In-House Pentest is a pentest that an organization performs on the Cobalt platform without involving Cobalt pentesters. The workflow for In-House Pentests is similar to other pentests that you run on the Cobalt platform.
Getting Started
Set up an Asset
If you don’t yet have assets, set up an asset. An asset is a either a software component of value, such as a web application or API, or a network environment.
- You can run In-House Pentests on assets that you’ve already tested on the Cobalt platform.
- Learn more about the asset types we support.
Prepare for a Pentest
To avoid disrupting workflows in your organization, notify your team about the upcoming pentest. Learn how to prepare for a pentest.
Define who will work on the pentest:
- In-House Pentesters test your asset and report vulnerabilities. You can invite pentesters from your organization, a third-party company, or both.
- Pentest Team Members collaborate on the pentest and address findings. As an Organization Owner or Member, you need to have a Pentest Team Member role to collaborate on the pentest.
Create an In-House Pentest
As an Organization Owner or Member, you can set up an In-House Pentest—following the same steps as for other pentest types. Some parameters in the pentest wizard may slightly differ for In-House Pentests.
To launch an In-House Pentest:
- On the Pentests page, select Create a Pentest.
- To enroll in the beta program for the Pentest Management Platform, select Learn more, and then select Enter the Beta.
- Under In-House Pentest, select or create an asset that you want to test, and then select Continue.
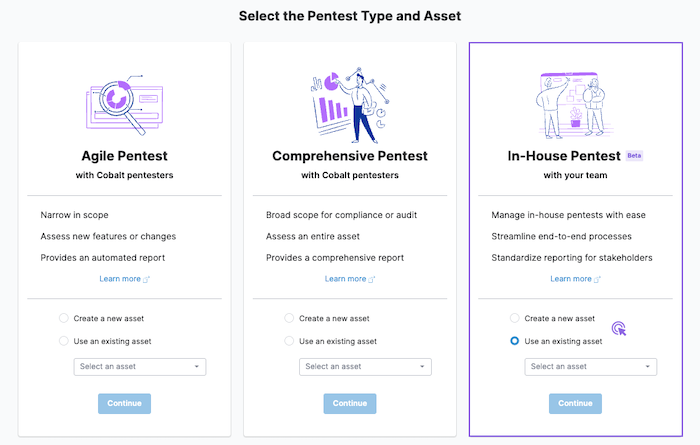
- In the pentest wizard, complete the following steps:
- Review your asset.
- Set requirements for your pentest.
- Define the details of your environment.
- Schedule the pentest by setting your desired start and end date. The start date and testing period are flexible.
- Review your pentest to make sure you’ve included all information that your pentesters need. When ready, select Move to Planned.
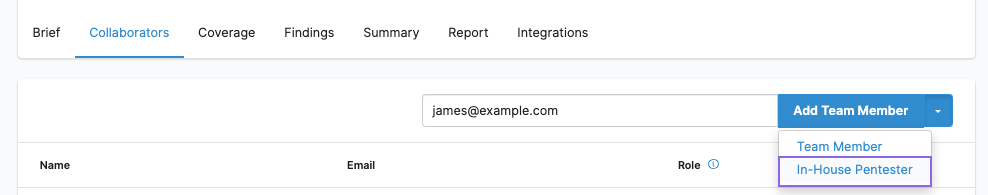
- Invite collaborators to the pentest. Select the key for instructions.
To add more collaborators, repeat these steps. You can add one user at a time.
If a user is already a Team Member on the pentest, you can change their role to In-House Pentester.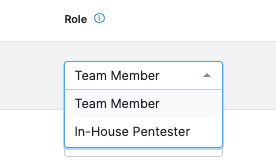
- When ready, select Launch Pentest. Your pentest goes Live.
- To launch a pentest, you need to assign at least one In-House Pentester.
Once the pentest goes Live, pentesters can start testing your asset. You can track the progress in real time.
Note
You can enable integrations, configure webhooks, and use the Cobalt API for your In-House Pentests.Collaborate on the Pentest
As a Pentest Team Member, you can collaborate on In-House Pentests to which you’re invited.
As an Organization Owner or Member, you automatically become a Pentest Team Member on all organization’s pentests, unless someone (including yourself) removes you.
Communicate in the Chat
Communicate with pentesters and team members in the chat throughout a pentest. To open the chat, select the chat icon on the pentest page.
Slack channels and Pentester Updates are not available for In-House Pentests.
Use the Coverage Checklist
The Cobalt coverage checklist is a list of checks that pentesters use throughout a pentest to ensure that a baseline of security controls are in place. The list is based on security standards such as OWASP Application Security Verification Standard (ASVS).
Learn more about the coverage checklist and how to use it.
Manage Pentest Collaborators
As a Pentest Team Member, you can add and remove team members from a pentest. Learn how to manage pentest users.
Move the Pentest to Remediation
If needed, you can move the pentest to Remediation before pentesters do so. Select Move to Remediation on the pentest brief.
When the pentest is in Remediation, pentesters can no longer submit new findings. The testing process is complete.
Users with the following roles can move a pentest to Remediation:
Remediate Findings
A finding is a vulnerability that a pentester reports during a pentest. To view findings, on the pentest page, navigate to Findings.
Once pentesters move a finding to Pending Fix, you can:
- Fix the finding and submit it for retest
- Mark the finding as Accepted Risk
Pentesters describe findings and provide recommendations on how to fix them. Navigate to the finding page for details.
You can start to remediate findings when the pentest is Live. You don’t need to wait until it’s in Remediation.
Submit a Finding for Retest
Once you’ve fixed a finding internally, you can submit it for retest. Learn how to submit a finding for retest.
Mark a Finding as Accepted Risk
Once you’ve analyzed a finding, you may want to accept it if:
- The risk associated with the vulnerability is low; or
- You plan to mitigate the finding in a way that doesn’t involve an actual technical fix.
Learn how to mark a finding as Accepted Risk.
Download the Pentest Report
Once the pentest report is ready, you get a notification. You can view and download the report on the Report tab.
- For In-House Pentests, you get the same report types as for Comprehensive Pentests.
- You can customize the contents of pentest reports.
- Learn more about the report contents.
What’s Next
Analyze the security posture of your assets based on the results of In-House and Cobalt PtaaS pentests.
- Navigate to Cobalt Insights to view aggregated data.
- Share pentest reports with stakeholders.
- Plan your next pentest to keep your security strong.