Release Notes: April 2024
Explore What’s New from Cobalt This Month
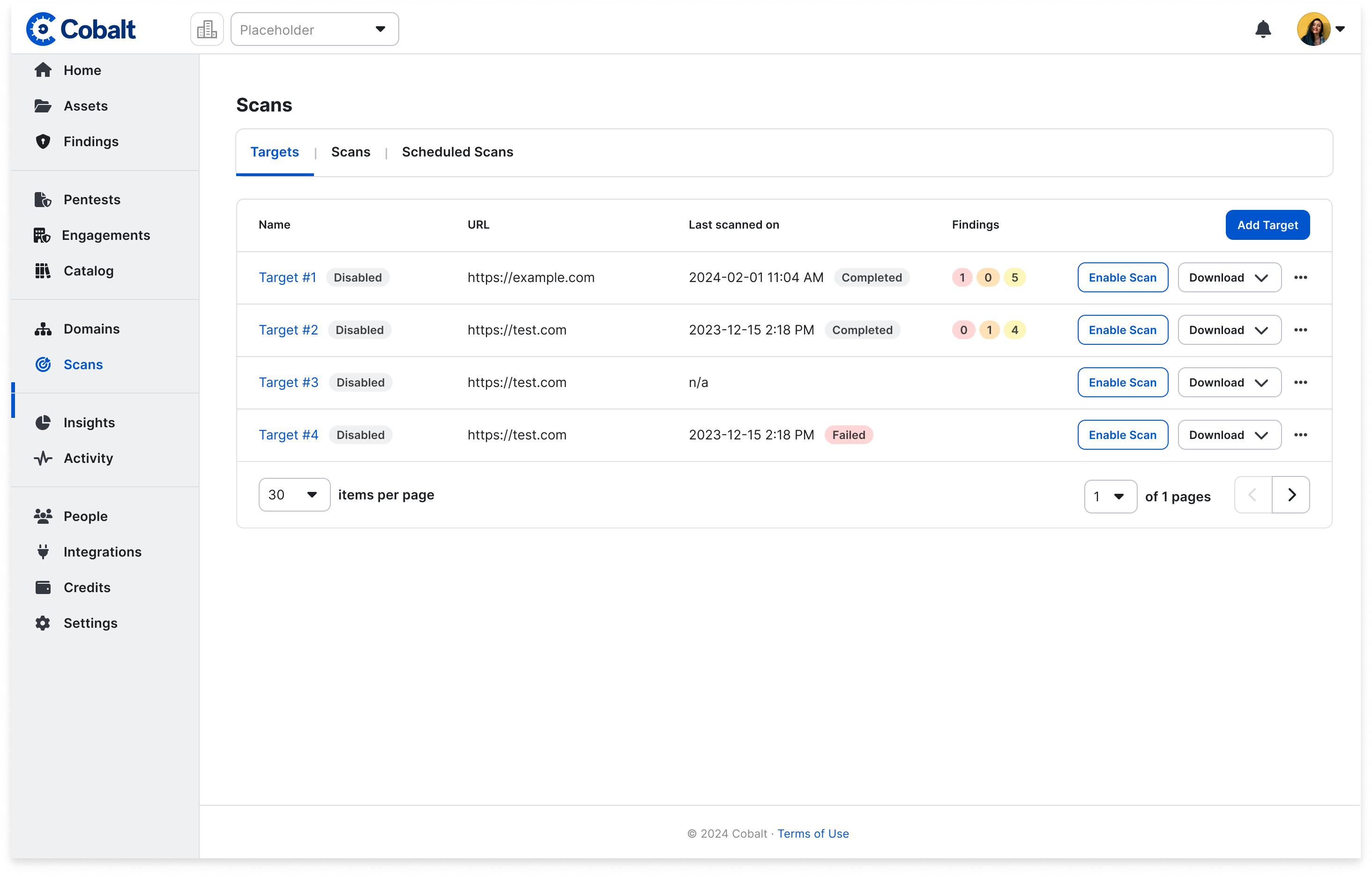
DAST Transition from Beta to General Availability
We are excited to announce that our DAST scanner is now officially out of beta and available for General Availability to all Cobalt customers. With this release, all customers can now leverage our new DAST scanner feature, allowing them to create an unlimited number of scans for one target. Please note that additional targets can be purchased as needed to expand your scanning capabilities.
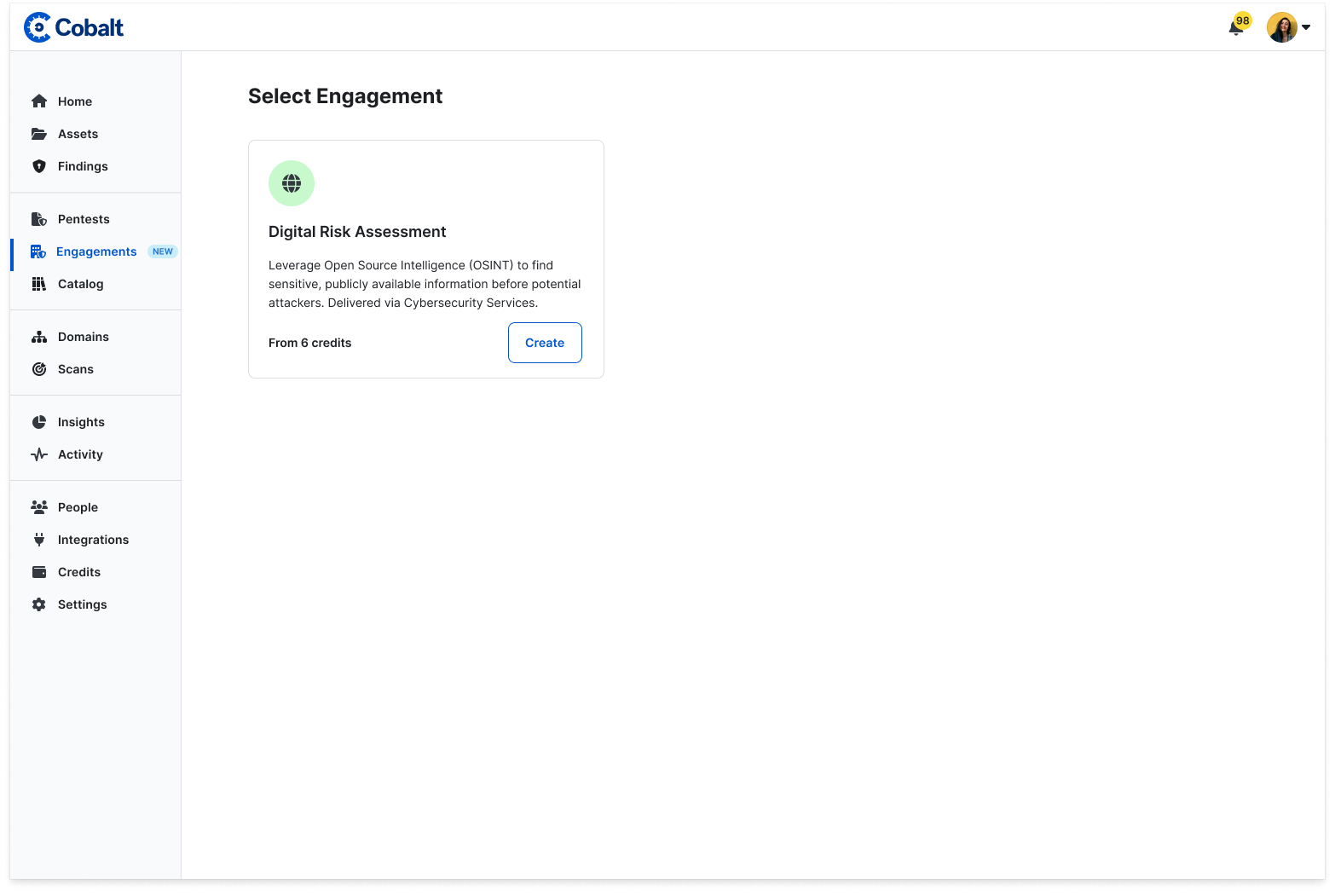
Cobalt Engagements: Introducing Digital Risk Assessments
We are thrilled to introduce Cobalt Engagements, a new platform feature that streamlines the process of conducting Digital Risk Assessments (DRA) and empowers customers to take control of their offensive security testing like never before.
Gone are the days of dealing with separate briefing documents, scoping questionnaires, and lengthy back-and-forth discussions to finalize a Statement of Work. With Cobalt Engagements, customers can now initiate a DRA engagement directly through our platform, simplifying and expediting the entire process.
What challenges does a DRA engagement solve for customers?
- Identifying Security Risks: Security teams must identify potential security risks and vulnerabilities that might be publicly accessible. Hackers often gather information from public sources to plan attacks. By understanding what information is out there, they can proactively mitigate these risks.
- Reputation Management: Monitoring online discussions and social media can help organizations manage their company’s reputation. Detecting and addressing negative sentiments early can prevent reputation damage, which can ultimately cost millions of dollars in damages and lost revenue.
- Phishing Prevention: By understanding what information about a company is publicly available, security teams can anticipate how attackers might craft phishing emails to target their employees or customers. This knowledge can be used to implement better security awareness training.
- Domain Protection: Asset discovery is crucial for identifying dangling domains previously owned and used by an organization before an attacker exploits for malicious activities including subdomain takeovers. Identifying these dormant assets is essential to maintaining the integrity of an organization’s online presence, ensuring all digital assets are accounted for and secured.
- Compliance and Regulation: Different organizations/industries have different compliance requirements for various regulations and industry standards and must prove they have taken both offensive and defensive measures to manage digital risk. Regular assessments can help these organizations identify if sensitive information is inadvertently being exposed, which might lead to compliance issues.
- Post-Incident OSINT Analysis or Breach Intelligence Analysis: After a breach, organizations may need to gather information about the attackers, their methods, and any additional threats they might face. This information can be valuable for understanding the scope of the breach, identifying the responsible parties, and preventing future incidents.